At Oneytrust we have teams specialising in Darkweb monitoring. They have observed a rise in the use of cloud storage to share the results collected by infostealers. Millions of login credentials of all kinds are made available to users. Here’s how to cope.
The threat of malicious “Infostealer” programs is becoming an increasingly concerning cybersecurity topic. Infostealers are malware designed to steal personal and sensitive information, such as login credentials, passwords, banking data, and any other confidential data stored on an infected device.
Understanding and addressing this type of threat is essential today for anyone using a computer, smartphone, or any other internet-connected device capable of running such programs. These malicious programs spread in various ways, most often by exploiting security vulnerabilities or using social engineering techniques to deceive users into downloading malware.
Once installed on a device, these programs can operate discreetly, stealing information without the user’s knowledge. The risks associated with an infostealer infection are numerous. Beyond personal information theft, users may fall victim to financial fraud, identity theft, or even extortion. Moreover, infostealers can compromise the security of devices and networks, paving the way for other types of malware and causing significant harm to both individuals and businesses.
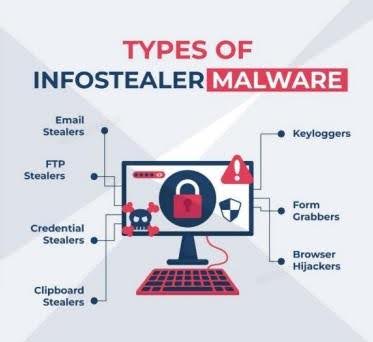
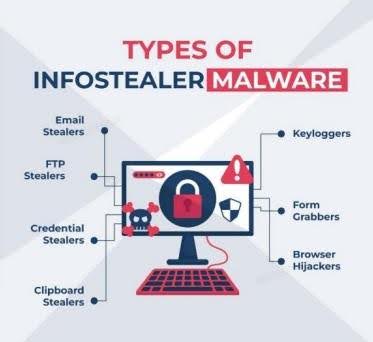
Here are the main types of infostealers:
At Oneytrust we have teams specialising in Darkweb monitoring. They have observed a rise in the use of cloud storage to share the results collected by infostealers. Millions of login credentials of all kinds are made available to users.
Most of the credentials are presented in ULP format for URL, Login, and Password:
- ➢ https://accounts.xxx.com/login:[email]:[password]
- ➢ https://auth.xxx.com/login:[username]:[password]
It’s worth noting that a significant amount of data is accessible for free. When users want full access to the compromised data, they must pay a subscription fee for privileged access.
We have seen that data compromised through infostealers is increasingly being exploited and shared across networks, particularly on Telegram through various groups created by malicious actors.
This data can target specific applications, such as financial management software, e-commerce apps, online gaming apps, and other applications that store personal and financial information. Due to their ability to adapt and evolve, Infostealers can potentially target any system, software, or application that stores or processes sensitive data.
It is therefore crucial for administrators and users of all operating systems and platforms to understand the risks associated with these malicious programs and to implement adequate security measures to protect themselves.
Here are essential measures to minimise the impact of this type of attack:
- Enforce multi-factor authentication (MFA) wherever critical data is stored.
- Implement a password management policy requiring employees to periodically change their passwords.
- Train and raise awareness among employees about best practices so they can understand the risks associated with high-risk applications.
- Immediately deactivate the accounts of former employees upon their departure.